I recently got an Intel(r) Express 530T switch from eBay. It's a "Manageable" switch, this means that you can connect to the switch through a null modem cable, telnet or a web interface to modify the switch configuration (Change MAC address filtering, create/delete VLANs, change ports speeds an priority, ...).
But when I tried to connect to the switch, I discovered that the switch hadn't been reseted, and that the seller didn't gave me the username and password needed to manage the switch.
After trying to find any reset button around, under, and even inside the switch, I sent a mail to the seller and contacted the Intel support.
As the seller wasn't responding and the Intel support wasn't able to give me a reset procedure, I crawled the web, and managed to find a little Intel(r) utility "that does not exists", according to the russian website that was distributing it (sorry, I can't remember the address).
This utility compute a backdoor password depending of your switch's MAC address.
The documentation that can be found with this Intel(r) utility, says that it works with :
- Intel(R) Express 330T Hub with Management Module
- Intel(R) NetStructure(TM) 470T/470F Switches
- Intel(R) Express 460T Standalone Switch
- Intel(R) Express 530T/535T Stackable Switches
It also says that you must let the usename blank, and just enter the password and that the backdoor password only works from the management port on the switch (It will not work through telnet nor the web interface).
So, after getting a password for my switch, I started to look at the password generation algorithm.
Here is the code of the password generation function :
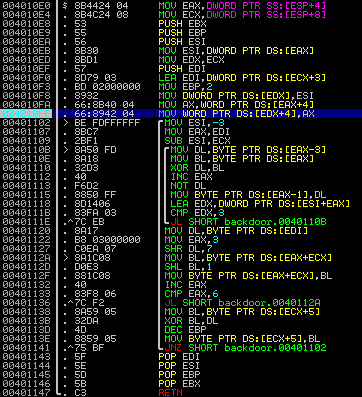
After reading this code, I managed to draw this little diagram of the generation algorithm:
(Saying M1 to M6 are the 6 MAC address bytes; xor is an exclusive or between two bytes; ! is a bit swapping of all bits eg: all 0s become 1s and all 1s become 0s; shl1 is a left shift of 1 bit; shr7 is a right shift of 7 bits)
After running this transformations two times on the buffer originally containing the switch MAC address, the password is the hexadecimal representation of M4,M5,M6.
Thus, for example, if M4=0xA0, M5=0×55 and M6= 0xEF, the password will be : A055EF.
Note: letters are always in uppercase.
Here you can find an implementation of this algorithm :
I hope you enjoyed this post as much as I enjoyed writing it ;)

Comments !